Recent
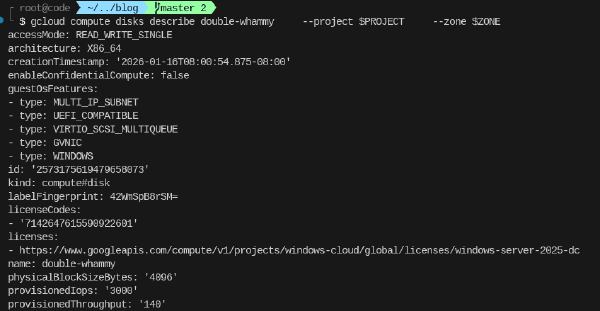
Updating Windows Server license version on GCE
·355 words·2 mins
When deploying a VM running certain operating systems such as Windows Server, a license is added to the boot disk of that instance. This license is used for billing PAYG licensing.
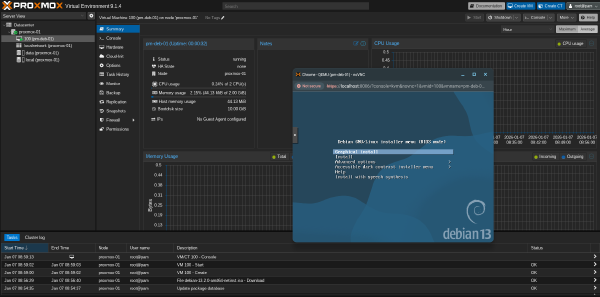
Running Proxmox PVE on Google Cloud using GCE (bare-metal) instances
·1565 words·8 mins
This article lays out the steps to prepare an image that can be used for GCE and GCE bare-metal instances to run Proxmox Virtual Environment (PVE). PVE is a solution similar to VMware and Nutanix that allows for management of fleet of VMs. Especially for scenarios like datacenter exits or migrations from on-premises customers look for solutions that allow them to easily transition to a virtualization solution if they are not ready for standard Google Compute Engine (GCE) VMs or if there are technical constraints that requires them to explore alternatives.
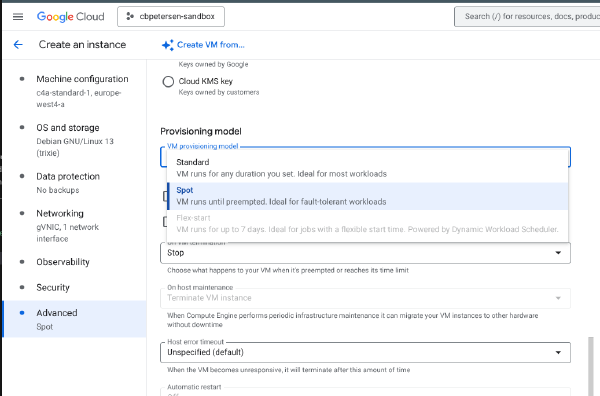
Changing Standard VMs to Spot provisioning model
·140 words·1 min
In a previous article I have explained how to change the provisioning of a VM from being preemtible to Standard. There are situations where you have a VM deployed with the Standard provisioning model but you want to reduce its cost and the workload is stateless or interruptible.
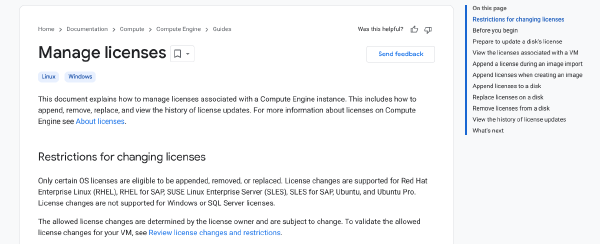
Changing licensing from BYOL to PAYG for Windows Server on Google Compute Engine
·409 words·2 mins
Customers moving Windows Server workload to the cloud often leverage bring your own license (BYOL) to optimize licensing cost. At some point customers may decide to change the licensing model. Reasons could be restrictive licensing terms constraining which versions can be deployed or optimizations such as reducing the amount time a VM and by extension the licese is running per month, for which a permanently assigned license is not the ideal choice.
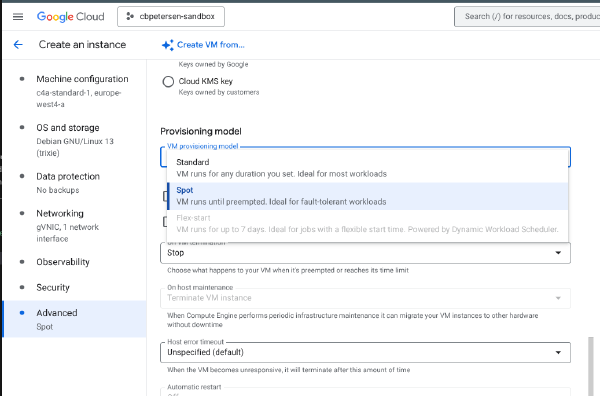
Changing provisioning model for Spot VMs
·234 words·2 mins
Spot VMs is a great way to reduce cost for interruptible, stateless and fault-tolerant workloads like batch processing or containers. Starting these types of VMs follows the same principles as regular VMs. The following snippet launches a C4A Spot VM:
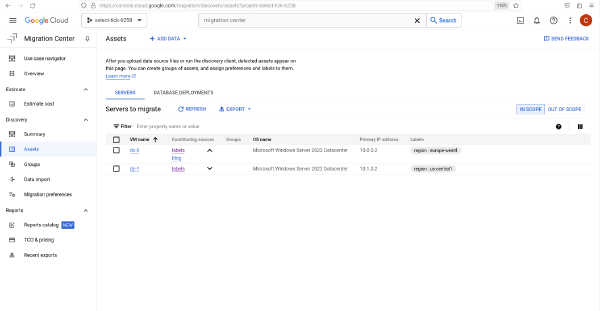
Labeling at scale in Google Cloud Migration Center
·652 words·4 mins
Google Cloud Migration Center is a great way to understand the total cost of ownership (TCO) for a migration to Google Cloud by running automatic assessments or uploading information about an estate using the output of tools such as RVTools.
Deterministically creating service identities for APIs in Google Cloud
·175 words·1 min
Platform services in Google Cloud act in the context of a service account. While these default service identities are mostly generated automatically, it is not always deterministic when they are created. Some are created when the API is enabled, others will only be created on first use of the API. This makes it hard for managing IAM permissions for these identities - especially when employing infrastructure as code like Terraform.
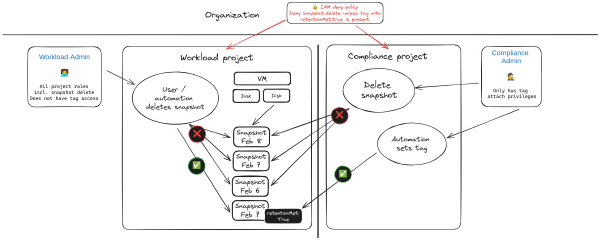
Protect disk snapshots against accidental deletion or malicious tampering
·1421 words·7 mins
It could happen. Total mahem. An administrative pricipal for a project was accidentally leaked. An attacker has taken you projects hostage. You need to recover and fast. Restoring project access is the least of your worries your concern is to restore services. Luckily you have all workloads protected with snapshots! All deleted by the attacker! This is an exaggerated and hypothetical scenario but I have seen similar things happening. In this article I’m exploring an approach to protect against such a scenario.
Call Cloud Workflow from Cloud Scheduler with Terraform
·418 words·2 mins
Cloud Workflows provide an easy way for platform automation and integration without the need to write any code. It also integrates seamlessly with Event Arc and other platform components.
Removing (unclaiming) disks from Storage Spaces Direct (S2D)
·310 words·2 mins
When running Storage Spaces Direct in Cloud environments where disk resources can be provisioned at a moments notice with any capacity, it can be the norm that disks will be (hot) added from a cluster to account for growing capacity or performance needs.

